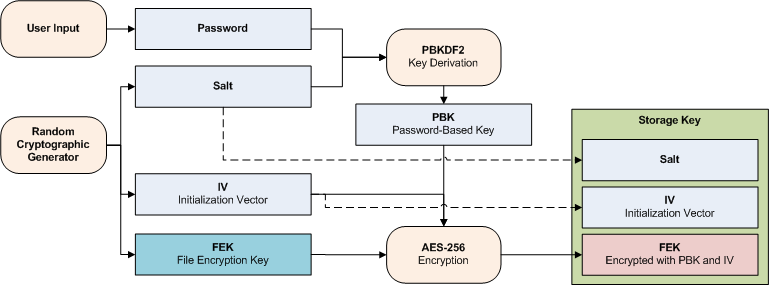
Encryption
Sep 5, 2017
Initialization
- A random cryptographic generator supplies a FEK (File Encryption Key). qBackup uses the FEK to encrypt files to be backed up.
- PBKDF2 (Password-Based Key Derivation Function 2) generates a PBK (Password-Based Key) from the password supplied by a user and the salt supplied by the random cryptographic generator. PBKDF2 uses HMAC-SHA256, a 256-bit salt and 100,000 iterations.
- The FEK is encrypted with AES-256 using the PBK and the IV (Initialization Vector) supplied by the random cryptographic generator.
- A storage key is created from the salt, the IV and the encrypted FEK. The storage key is stored in a backup destination.
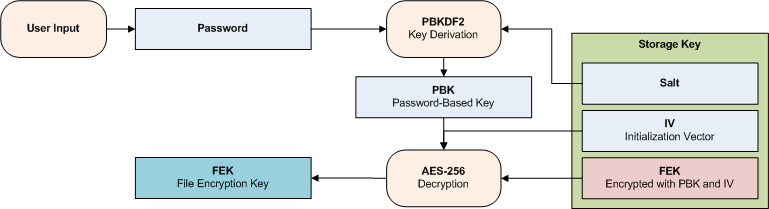
Retrieving the file encryption key
- qBackup loads the storage key from the backup destination.
- PBKDF2 generates the PBK from the password supplied by the user and the salt in the storage key.
- The FEK is decrypted with AES-256 using the PBK and the IV in the storage key.
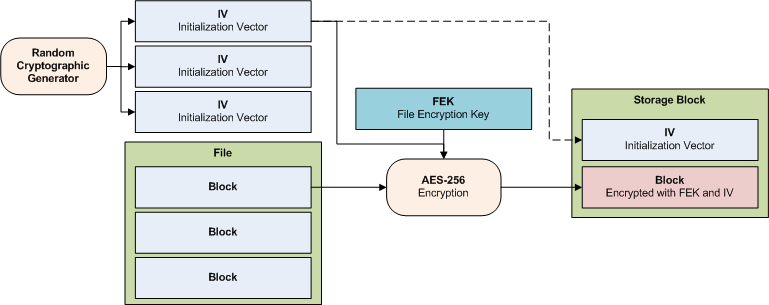
File encryption
- qBackup divides a file into blocks. Each block is processed as follows.
- The block is encrypted with AES-256 using the FEK and the IV supplied by the random cryptographic generator. A unique IV is generated for each block.
- A storage block is created from the IV and the encrypted block. The storage block is stored in the backup destination.
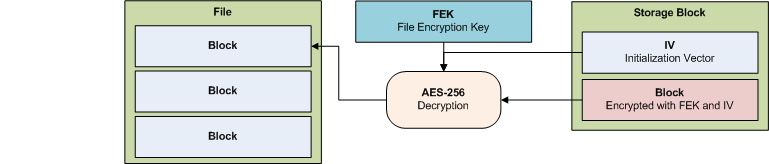
File decryption
- qBackup loads storage blocks constituting a file from the backup destination. Each storage block is processed as follows.
- The encrypted block is decrypted with AES-256 using the FEK and the IV.
- qBackup writes the block to the file.